-
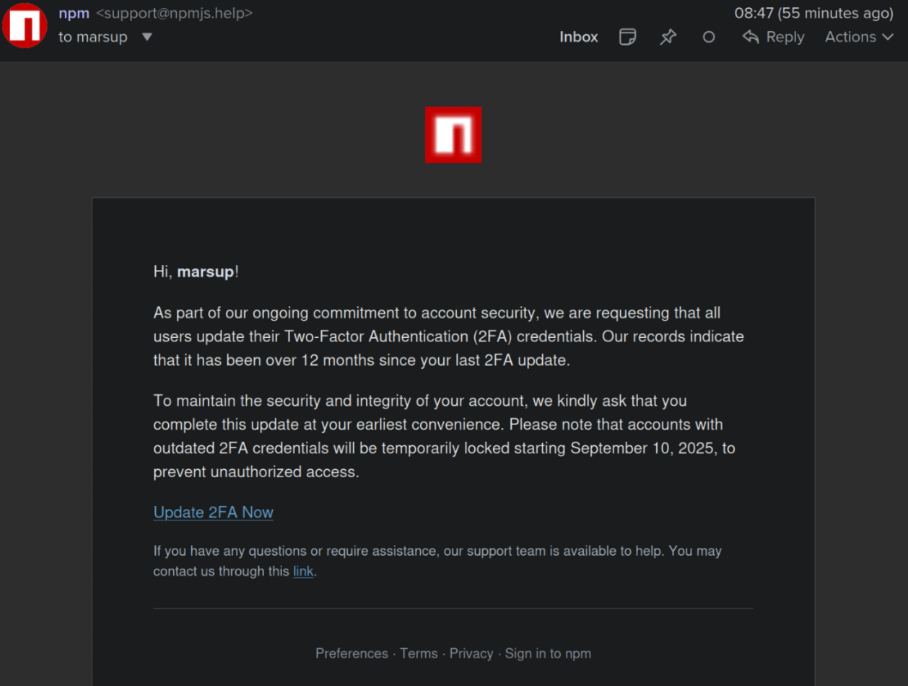
At least 18 popular JavaScript code packages that are collectively downloaded more than two billion times each week were briefly compromised with malicious software today, after a developer involved in maintaining the projects was phished. The attack appears to have been quickly contained and was narrowly focused on stealing cryptocurrency. But experts warn that a…
-
A threat actor is using a sophisticated EDR-killing malware tool in a campaign to maintain long-term, persistent access on Windows systems. Read More
-
The breach kickstarted a massive supply chain attack that led to the compromise of hundreds of Salesforce instances through stolen OAuth tokens. Read More
-
A threat actor possibly of Russian origin has been attributed to a new set of attacks targeting the energy sector in Kazakhstan. The activity, codenamed Operation BarrelFire, is tied to a new threat group tracked by Seqrite Labs as Noisy Bear. The threat actor has been active since at least April 2025. “The campaign is…
-
A new set of four malicious packages have been discovered in the npm package registry with capabilities to steal cryptocurrency wallet credentials from Ethereum developers. “The packages masquerade as legitimate cryptographic utilities and Flashbots MEV infrastructure while secretly exfiltrating private keys and mnemonic seeds to a Telegram bot controlled by the threat actor,” Socket researcher…
-
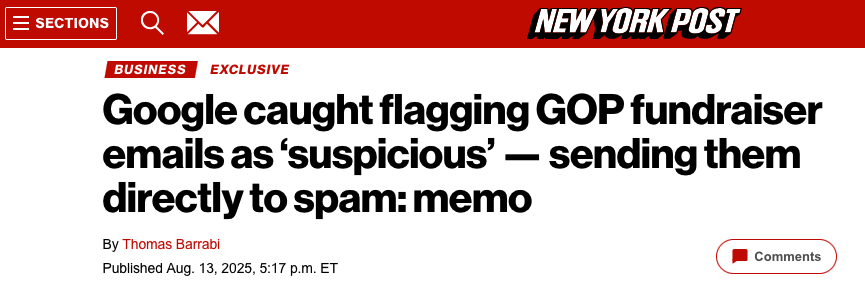
The chairman of the Federal Trade Commission (FTC) last week sent a letter to Google’s CEO demanding to know why Gmail was blocking messages from Republican senders while allegedly failing to block similar missives supporting Democrats. The letter followed media reports accusing Gmail of disproportionately flagging messages from the GOP fundraising platform WinRed and sending…
-
Experts agree there have been subtle improvements, with new laws and applied best practices, but there is still a long way to go. Read More
-
Exploitation of CVE-2025-42957 requires “minimal effort” and can result in a complete compromise of the SAP system and host OS, according to researchers. Read More
-
The biggest vulnerabilities may lie at the boundaries of where the AI agent connects with the enterprise system. Read More
-
The vulnerability marks the latest example of threat actors weaponizing exposed ASP.NET machine keys for remote injection and deserialization attacks. Read More