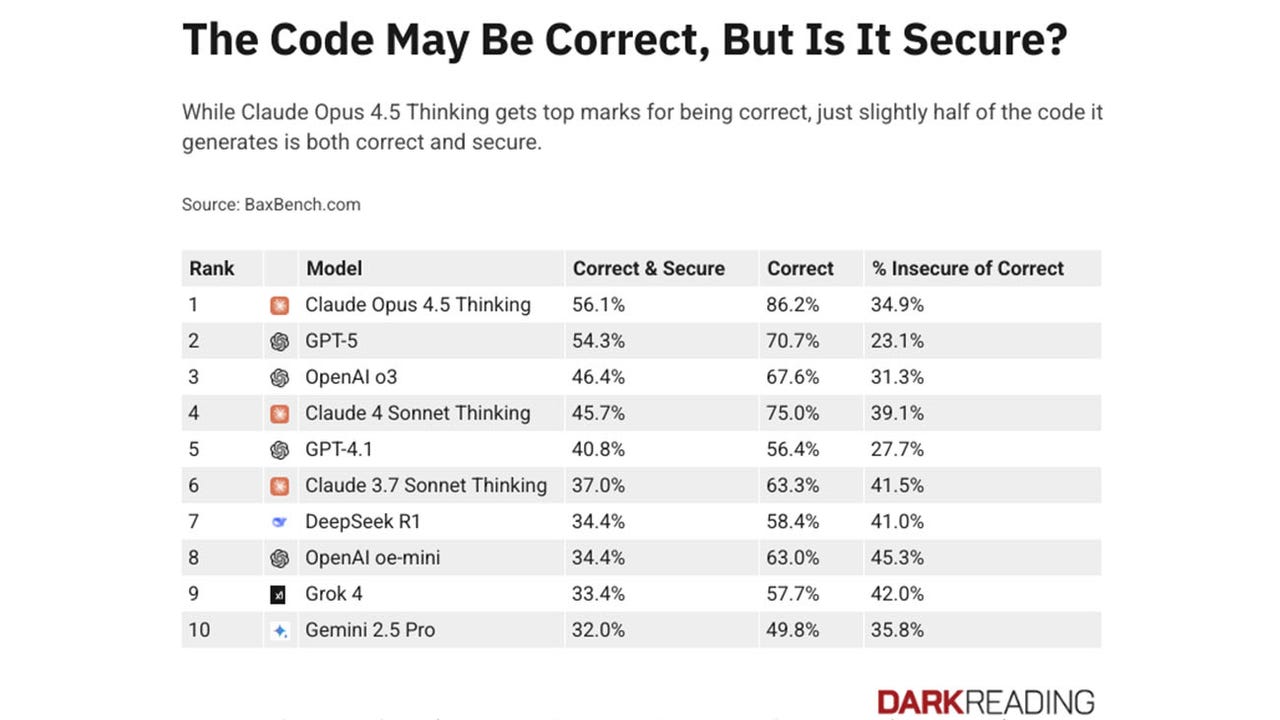
-
Developers are leaning more heavily on AI for code generation, but in 2026, the development pipeline and security need to be prioritized. Read More
-
Take part in the new survey from Dark Reading and help uncover trends, challenges, and solutions shaping the future of application security. Read More
-
ThreatsDay Bulletin: Stealth Loaders, AI Chatbot Flaws AI Exploits, Docker Hack, and 15 More Stories
It’s getting harder to tell where normal tech ends and malicious intent begins. Attackers are no longer just breaking in — they’re blending in, hijacking everyday tools, trusted apps, and even AI assistants. What used to feel like clear-cut “hacker stories” now looks more like a mirror of the systems we all use. This week’s…
-
The encrypted vault backups stolen from the 2022 LastPass data breach have enabled bad actors to take advantage of weak master passwords to crack them open and drain cryptocurrency assets as recently as late 2025, according to new findings from TRM Labs. The blockchain intelligence firm said evidence points to the involvement of Russian cybercriminal…
-
Statistics across all threats In Q3 2025, the percentage of ICS computers on which malicious objects were blocked decreased from the previous quarter by 0.4 pp to 20.1%. This is the lowest level for the observed period. Percentage of ICS computers on which malicious objects were blocked, Q3 2022–Q3 2025 Regionally, the percentage of ICS…
-
Fortinet on Wednesday said it observed “recent abuse” of a five-year-old security flaw in FortiOS SSL VPN in the wild under certain configurations. The vulnerability in question is CVE-2020-12812 (CVSS score: 5.2), an improper authentication vulnerability in SSL VPN in FortiOS that could allow a user to log in successfully without being prompted for the…
-
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added a security flaw impacting Digiever DS-2105 Pro network video recorders (NVRs) to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability, tracked as CVE-2023-52163 (CVSS score: 8.8), relates to a case of command injection that allows post-authentication remote code Read…
-
Cybersecurity researchers have discovered a new variant of a macOS information stealer called MacSync that’s delivered by means of a digitally signed, notarized Swift application masquerading as a messaging app installer to bypass Apple’s Gatekeeper checks. “Unlike earlier MacSync Stealer variants that primarily rely on drag-to-terminal or ClickFix-style techniques, this sample adopts a more …
-
The fraudulent investment scheme known as Nomani has witnessed an increase by 62%, according to data from ESET, as campaigns distributing the threat have also expanded beyond Facebook to include other social media platforms, such as YouTube. The Slovak cybersecurity company said it blocked over 64,000 unique URLs associated with the threat this year. A…
-
Every year, cybercriminals find new ways to steal money and data from businesses. Breaching a business network, extracting sensitive data, and selling it on the dark web has become a reliable payday. But in 2025, the data breaches that affected small and medium-sized businesses (SMBs) challenged our perceived wisdom about exactly which types of businesses…

_Yuri_Arcurs_alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)







